What to do with an MD5 Hash?
国外一站上看到的。
Author:Holz
From: http://www.overclock.ch/forum/viewtopic.php?t=46
Let’s use 7cf2db5ec261a0fa27a502d3196a6f60 (= pizza) as example MD5 hash.
1. KOP’s Database on IRC (Rizon)
Simply connect to Rizon (irc.rizon.net) and join #md5 / #md5crack with your IRC client.
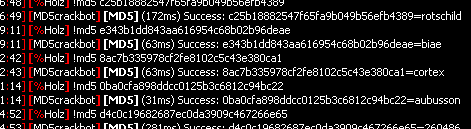
[%MD5crackbot]
[MD5] I accept the following triggers: !help !hp !dbinfo !donate – !md5 .md5 or ?md5 <hash>. To hash a text, use !hash .hash or ?hash <text>. If you want to avoid flooding here, join #md5crack – Thanks.
[%MD5crackbot] [MD5] Other triggers: !google <searchterm> !wiki <searchterm> !country <tld>[/quote]
2. MD5 Library on AIM (AOL Instant Messenger)
If you don’t have AIM yet you can get it on http://www.aim.com/.
Now simply message the hash to “MD5 Library” and hope it knows the plain text.
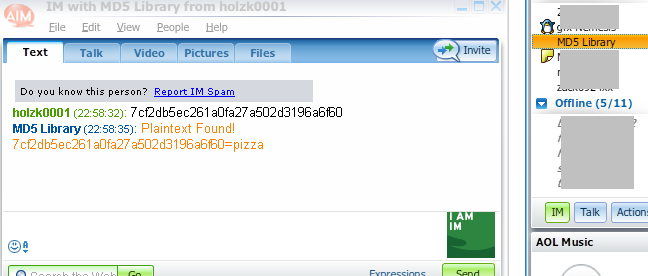
There we go. I like the MD5 Library because it just knows a lot of hashes.
The bot has some more functions, by the way.
Type help to get a list of commands… the bot also chats with you if you want to.
3. Online Databases
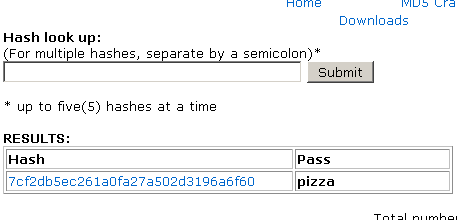
I’m just gonna tell you some online databases. If you check the first one or two it should be fine already.
* http://gdataonline.com/seekhash.php – GData: An Online MD5 Hash Database
* http://md5.rednoize.com/ – md5(); – reverse engineer md5 hashes
* http://md5.overclock.ch/biz/index.php?p=md5crack&l=en – MD5crack v2 by [KOP]
* http://nz.md5.crysm.net/ – md5 reverse lookup [NZ]
* http://us.md5.crysm.net/ – md5 reverse lookup [US]
* http://www.md5decrypt.com/ – MD5 Decrypt
* http://shm.hard-core.pl/md5/ – md5 hash database project
* http://www.und0it.com/ – Premiere MD5 Crack Service (Registration Required)
* http://www.milw0rm.com/cracker/insert.php – free md5/lm hash cracking
* http://rainbowtables.net/services/results.php?selector=4 – Bulk Password Decryption Results
* http://ice.breaker.free.fr/ – Ice Breaker : Online MD5 Reverser | SHA1 Reverser || …
Now there are many more databases but these should be enough… and as I said before, if you check the first one or two it will be fine.
4. Dictionary Attack (using Cain)
If you don’t have Cain yet you can get it from http://www.oxid.it/cain.html.
Open Cain, go to Cracker, go to MD5 Hashes, insert your MD5 hash(es), right click on the hash(es), select Dictionary Attack.
The following window will appear:
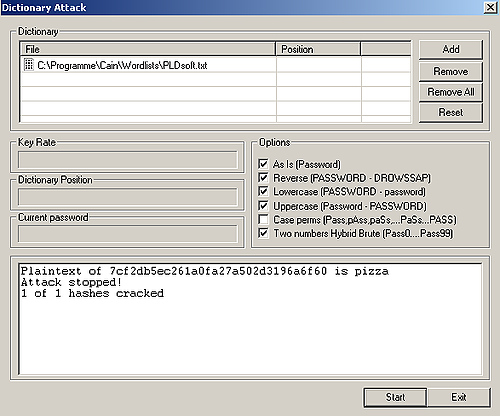
As you can see you just have to select the word list(s), configure the options and click on Start.
If you need word lists check out these two links.. if you still need more just search on the forums and google.
* http://www.zack6924-underground.net/forum/admin/adminusers/holz/ha/Wordlists_OLD-HOLZ.rar
* http://packetstorm.security-guide.de/Crackers/wordlists/
* ….
5. Bruteforce Attack (using Cain)
First of all: Keep ind mind that a bruteforce attack can take a very long time!
This is very similar to the Dictionary Attack.
You just have to select Brute-Force Attack instead of Dictionary Attack when right-clicking the hash(es).
The following window will appear:
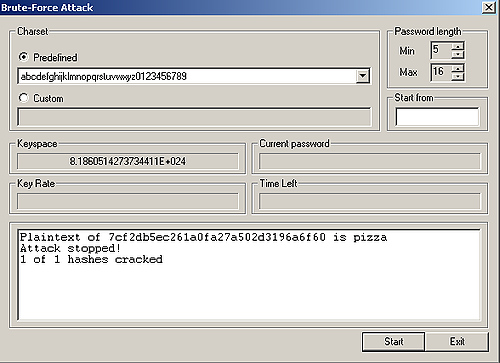
As you can see you just have to configure the options the way you like and click Start.
That’s it. I hope this helps the one or the other user and I don’t have to tell this to everyone separately.