Microsoft Windows Cursor and Icon Format Remote Code Execution (0day)
鬼仔注:昨天发的那个IE 0day,现在有细节了,生成器也有人放出来了。文章尾部附生成器下载
是一些特殊的.ani鼠标指针文件,伪装成.jpg。
微软官方的公告:Microsoft Security Advisory (935423): Vulnerability in Windows Animated Cursor Handling
来源:Ph4nt0m Security Team
就是最新那个ie 0day了,实际上利用方法不止是ie,用winhex等打开都会中,问题似乎是出在
user32.dll 的 loadcursorxxxxxxx ,函数返回时crash。
用资源管理器打开那个目录也可以触发,和以前的ms06-001 wmf漏洞有些相象,危害非常大。
Frsirt描述如下:
A vulnerability has been identified in Microsoft Windows, which could be exploited by remote attackers to take complete control of an affected system. This issue is due to a memory corruption error when rendering malformed cursors, animated cursors or icons, which could be exploited by remote attackers to execute arbitrary commands by tricking a user into visiting a malicious web page or viewing an email message containing a specially crafted ANI file.
Note : This zero-day vulnerability is currently being exploited in the wild.
Frsirt还把这个当钱卖,但是已经在网上有人公开生成器了。
http://www.hackeroo.com/read.php?tid-3014.html
另外,这个漏洞是影响VISTA的!
Affected Products
Microsoft Windows 2000 Service Pack 4
Microsoft Windows XP Service Pack 2
Microsoft Windows XP 64-Bit Edition ersion 2003 (Itanium)
Microsoft Windows XP Professional x64 Edition
Microsoft Windows Server 2003
Microsoft Windows Server 2003 (Itanium)
Microsoft Windows Server 2003 Service Pack 1
Microsoft Windows Server 2003 SP1 (Itanium)
Microsoft Windows Server 2003 x64 Edition
Microsoft Windows Vista
Microsoft Internet Explorer 6
Microsoft Internet Explorer 7
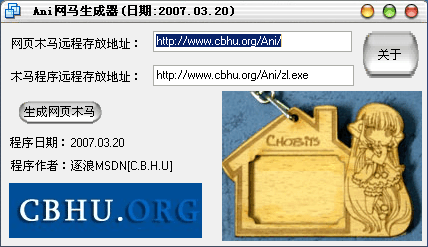
生成器下载地址: http://www.51files.com/?QGLEK7WJHY3G7I6G4NL6
活见鬼,,,XXX
:???: 又见到丰子,XXX
那个下载站的速度慢的真够可以的了!!!!!
受教了.
怎么抽出那个ANI文件呢?这样才能试试怎么做免杀.
里面那个jpg就是了
JPG不好免杀.
应该说是.ani 不知道有什么新思路..
谁能提供下呢……….
不是jpg,是ani